If you're reading this article, you probably know that open-source investigation (OSINT) is used for a variety of purposes, from checking a person's background to predicting customer behavior.
However, using OSINT to enhance cybersecurity is likely the most important goal for several reasons:
- A high level of cybersecurity saves companies and their customers from much trouble due to data breaches.
- Data protection ensures that companies' assets and money cannot be stolen.
- The task of cyber security is to protect work processes from interruptions due to malware.
While OSINT is not the only way to protect systems and data, it significantly impacts how IT professionals address security breaches. Let's look at how OSINT works in this area.
How is OSINT used in cybersecurity?
OSINT specialists use different methods and techniques to ensure companies' security and their systems. We will consider the main ones.
OSINT specialists collect public information that creates vulnerabilities
A person leaves much information on the network (digital footprint) that hackers can use to hack their pages and steal personal data. For example, it can be an email address, a phone number, reports from work events, or posts about successful agreements. When there are dozens of such people in the company, the probability of hacking grows.

Moreover, often managers unintentionally leave information about the company or employees in the public domain. For example, documents with contacts, examples of contracts, or information about their site’s domains and managers can get into the network. If the company has not banned its data indexing, it is also relatively easy to find them using Google or other popular search engines.
So, the task of OSINT specialists is to search for such information and hide it so that hackers cannot use it.
OSINT specialists collect public information to detect data leakage
If your company has security issues, the chances that your data can be found online are high. OSINT specialists usually check the dark web for leaked databases related to their company, as they are sold there.

Having discovered the leaked data, the specialist tries to remove them from public access and guess how and where they were stolen. As a result, having checked their assumptions, the specialist discovers security breaches and fixes them.
OSINT specialists check systems with advanced tools
OSINT specialists can also use special tools to check the availability of data about the structure and operation of the software, site, or connected devices. For example, some tools will allow you to see the decryption of protocols, ports, and the protection of devices connected to the Internet. If a specialist detects any potential threats, they can eliminate them by hiding information or putting up double protection.
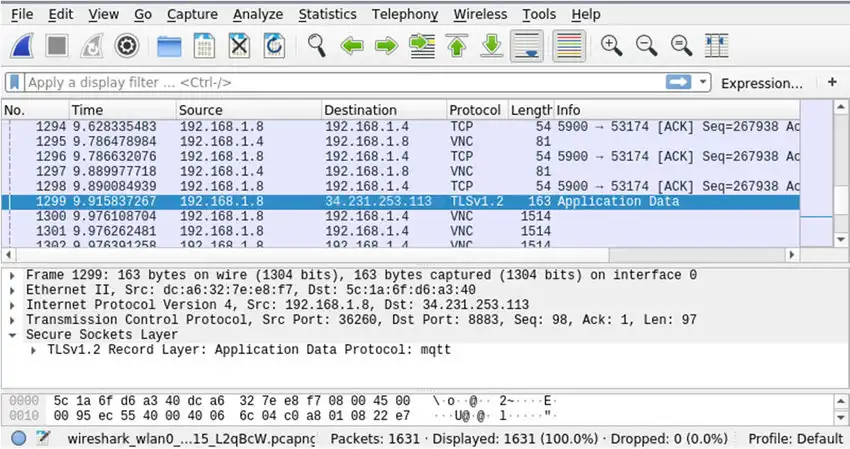
What security threats does OSINT protect against?
Now that you know how OSINT is used in cybersecurity, let's look at what threats it prevents. There are many variants of hacker attacks, but we will divide them into groups to make the information easier to understand.
Phishing
Phishing is the easiest way for hackers to get your data, although not the most reliable. Let's look at an example.

Hackers find your employees' emails from open sources and learn from the article that you have planned to move to a new office. They write an email offering your employees to take a survey and tell what they want to see in the new office. But they add a link to malware instead of a link to a survey. Employees follow the link, and malware steals their passwords or blocks their accounts.
That's what phishing is: hackers lure people into downloading malware, sending money, or providing their personal data in other ways. You can protect yourself from such attacks by finding and hiding information from public access and by teaching employees to recognize phishing attacks.
Penetration into open source programs
Companies often use open source applications, integrating them into their system. Their advantage is convenience and usually low price, but their main disadvantage is vulnerability. Hackers can easily open the code of such services and find flaws that can be used to block systems, gain access to them, or steal data.
Such problems are often discovered after a data breach, although they can be prevented by using special tools. In any case, a collaboration between OSINT and IT professionals makes open source software more secure.
Gaining access to systems using Common Vulnerabilities and Exposures (CVE)
Unfortunately, hackers can use open data as well as OSINT specialists. The Common Vulnerabilities and Exposures (CVE) database is one such open source that benefits both parties. All new vulnerabilities and exposures of various systems, networks, and devices are published in this database so that IT specialists can identify and fix them while improving the cybersecurity of their companies.
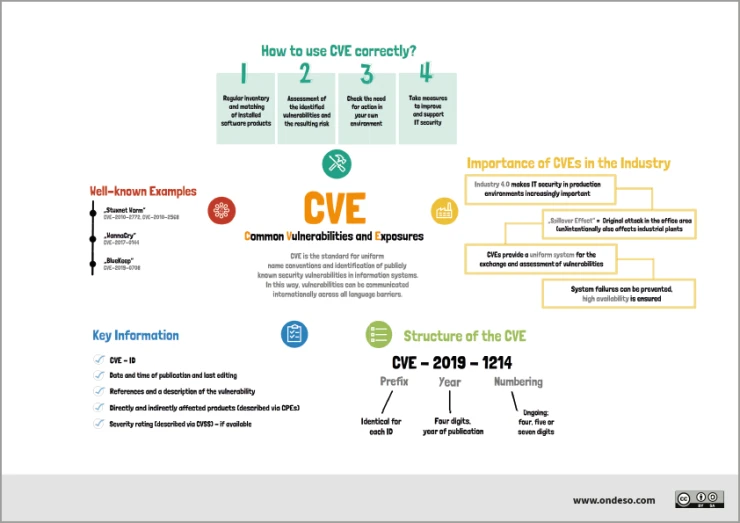
However, if OSINT or IT professionals do not use this opportunity, hackers can take advantage of it. For example, some programs can show a structure and a way of building software or a website, and if it is associated with one of the CVEs, a hacker can use it to penetrate the system. So, cybersecurity professionals need to regularly check for updates to this database to fix flaws in their software before hackers can take advantage of it.
Some OSINT cybersecurity tools
Since there are a lot of OSINT cybersecurity tools and they are used depending on the goals, we will not explain them in detail. Choose helpful ones by description from the list below and try to use them in practice.
- Google Dorks (Any site with Google Dorks you find online, for example): Provides more accurate search results. Free.
- Nmap: Discovers hosts and services on a computer network by sending packets and analyzing the responses. Free.
- BuiltWith: Shows technologies and platforms used to build a particular website. Has several paid plan options.
- Intelligence X: Searches for leaked data on the darknet, document shared platforms, and databases. Has several paid plan options.
- Maltego: Gather information from open sources and connects points between people, companies, or sites. Has demo and several paid plans.
- Wireshark: Analyzes network protocols at a microscopic level. Free.
- Shodan: Search information on devices connected to the Internet, including real-time data on security status and malware in the system. Has several paid options.
- Spyse: Provides information on domain including IPs, HTTP headers, robots.txt, and links. Checks vulnerability by comparing open ports with the CVE list. Has free and paid plans.
- Metagoofil: Extracts metadata from all types of open-sourced files. Free.
- Hunter.io: Finds email addresses by corporate domain. Gives 25 free searches for a month after registration.
Conclusion
OSINT is of great importance for cybersecurity as hackers can use open information to attack and steal private data. That's why the task of OSINT specialists is to search for this data and prevent the threats they create. The methods for accomplishing this task, as well as the tools, vary, so you can discover their benefits only by putting them into practice for specific purposes.
***
📌 For everyone who really wants to learn OSINT, we recommend OSINT training courses from Molfar:
▪️ Basic: for personal study and receiving a knowledge base + all the necessary tools for work.
▪️ Advanced: for scaling processes, gathering a team and learning HUMINT.




